The _________ controls focus on the response to a security breach, by warning of violations or attempted violations of security policies or the identified exploit of a vulnerability and by providing means to restore the resulting lost computing resources.
Fill in the blank(s) with the appropriate word(s).
detection and recovery
You might also like to view...
Multiple arguments to a function are separated by
a. comments b. semicolons c. colons d. commas e. periods
Assuming that x and y are equal to 3 and 2, respectively, after the statement x -= y executes, the values of x and y will be:
a. x: 5; y: 3 b. x: 3; y: -1 c. x: 3; y: 5 d. x: 1; y: 2
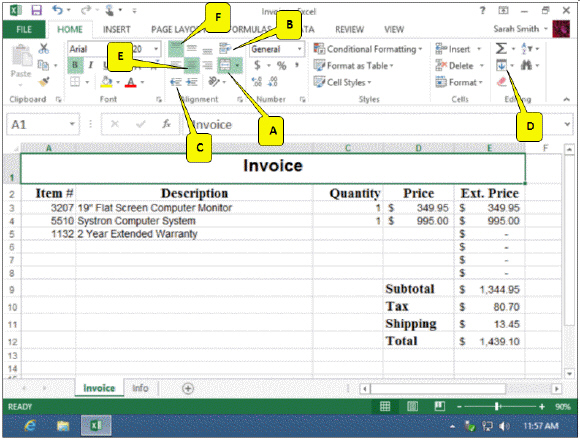 In the accompanying figure, which callout points to the button used to center cell contents?
In the accompanying figure, which callout points to the button used to center cell contents?
A. A B. B C. F D. E
Use the grep command to search the /usr/include/bits/socket.h file and display the lines that contain the string SOCK_. What command line did you use?
Use the grep command to search the /usr/include/bits/socket.h file and display the lines that contain the string SOCK_. What command line did you use?