The Rotate all text 90° option displays the text from bottom to top and is aligned at the lower left edge of the column
Indicate whether the statement is true or false
FALSE
You might also like to view...
In the 1970s, phone phreaks, a new sort of hacker, appeared. They used various methods, collectively called ____________________, to access telephone networks to make free calls from payphones.
Fill in the blank(s) with the appropriate word(s).
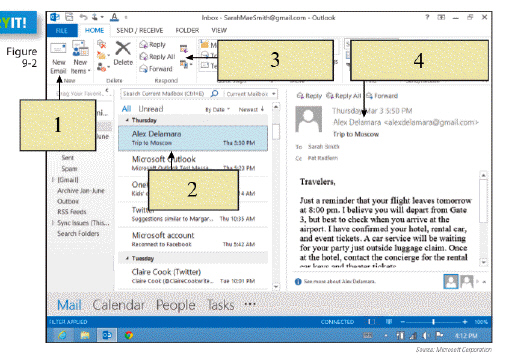 New mail is downloaded to the ____, represented by item 2 in the figure above.
New mail is downloaded to the ____, represented by item 2 in the figure above.
A. Write button B. message content C. Outbox D. Inbox
A(n) polymorphic threat is one that over time changes the way it appears to antivirus software programs, making it undetectable by techniques that look for preconfigured signatures. _________________________
Answer the following statement true (T) or false (F)
?Businesses started adopting Internet Explorer more than 20 years ago simply to view webpages. Today, Microsoft Edge has a different purpose: __________.
Fill in the blank(s) with the appropriate word(s).