A ____________________ mode VPN establishes two perimeter tunnel servers to encrypt all traffic that will traverse an unsecured network. The entire client packet is encrypted and added as the data portion of a packet addressed from one tunneling server to another.
Fill in the blank(s) with the appropriate word(s).
tunnel
You might also like to view...
Develop a strategy for coming up with a password that an intruder would not be likely to guess but that you will be able to remember.
What will be an ideal response?
________ is an expression that precisely defines the range of data that will be accepted in a field
A) Range expression B) Validation rule C) Data expression D) Validation text
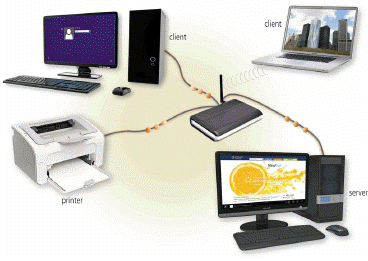
A. client base B. baseline C. network D. server farm
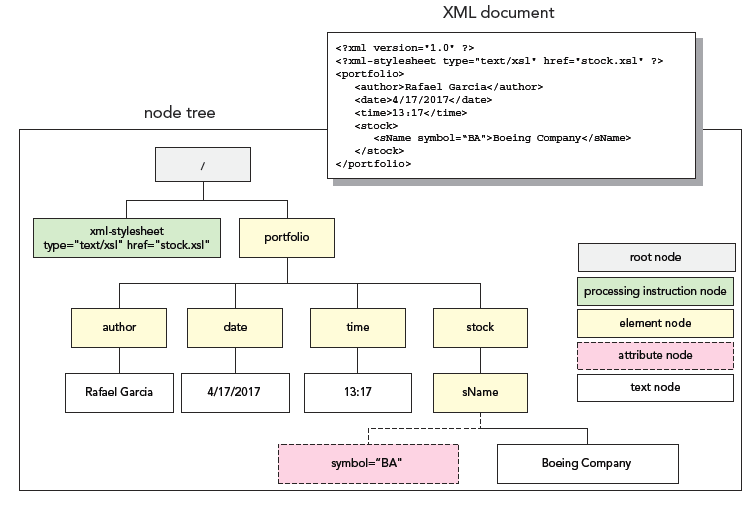
A. ?parent B. ?child C. ?sibling D. ?descendant