Holly is trying to use Windows Defender to run an antivirus scan. Windows Defender refuses to run. She notices a problem when she tries to update Windows Defender and it fails. When Holly opens the Action Center she sees this screen.
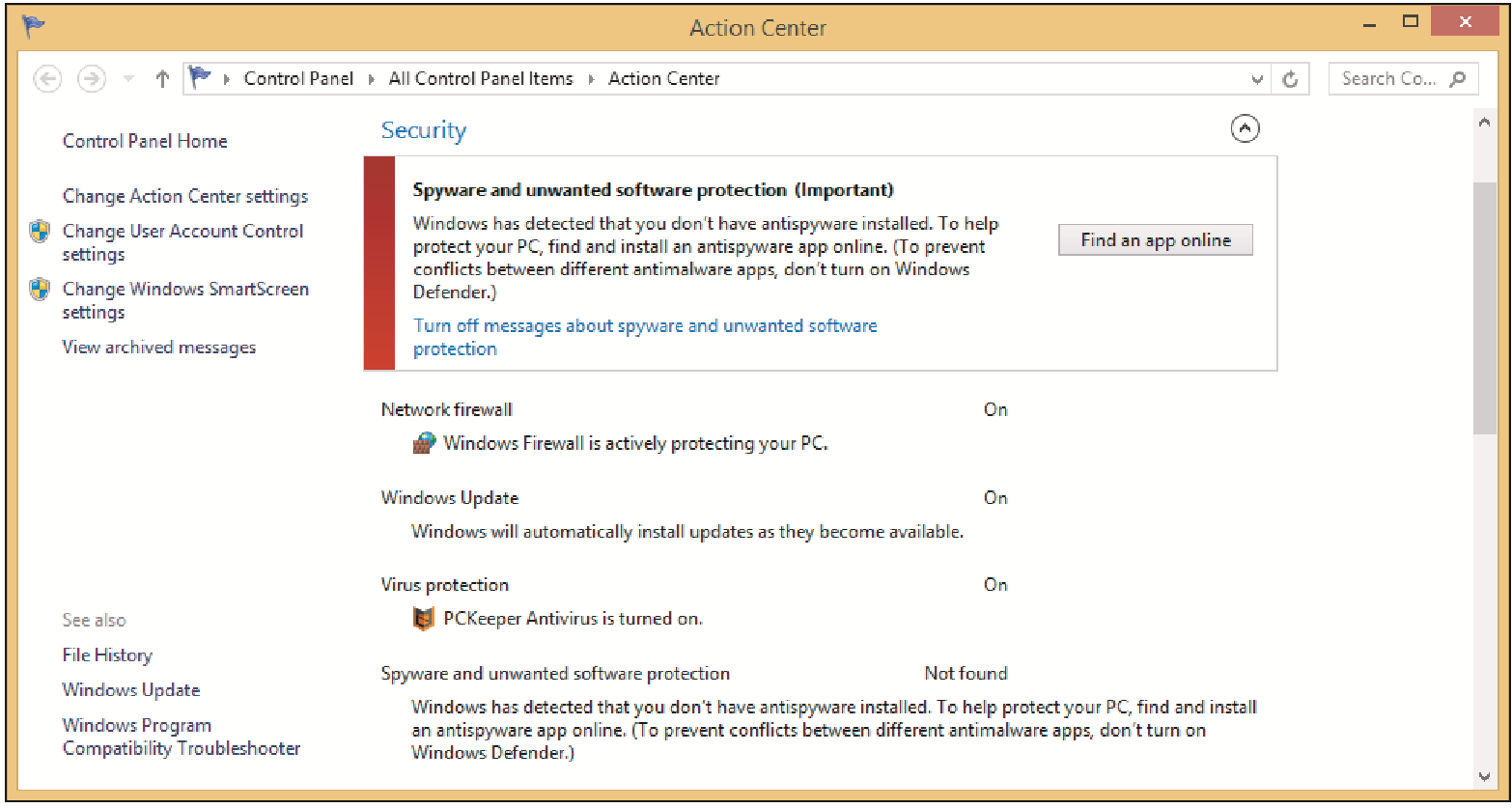
What has happened to Holly’s computer?
A. She has received a spam message.
B. She has received a security alert message.
C. Someone has hijacked her email.
D. She has downloaded a rogue antivirus.
Answer: D
You might also like to view...
Text that is formatted with options common to many applications such as Word and PowerPoint is called ________ text
A) enriched B) ASCII C) ANSI D) rich
The ____ Tool adjusts the borders of an image created from a camera raw file.
a. Border b. Adjustments c. Crop d. Filter
A physical control attempts to discourage security violations before they occur.
Answer the following statement true (T) or false (F)
Which queue operation does the following algorithm describe?Algorithm aQueueOperation allocate queue head set queue front to null set queue rear to null set queue count to 0 return queue headend aQueueOperation
A. empty queue B. dequeue C. create queue D. queue count