DNS poisoning can be prevented using the latest edition of what software below?
A. BIND
B. DHCP
C. WINS
D. finger
Answer: A
You might also like to view...
Which of the following statements is false?
a. A common way to perform synchronization is to use Java’s built-in monitors. b. Every object has a monitor and a monitor lock (or intrinsic lock). c. A monitor ensures that its object’s monitor lock is held by a maximum of two threads at a time. d. Monitors and monitor locks can be used to enforce mutual exclusion.
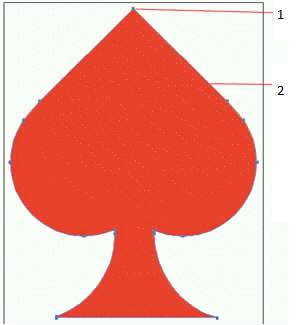 In the accompanying figure, item 2 points to a(n) ____________________.
In the accompanying figure, item 2 points to a(n) ____________________.
Fill in the blank(s) with the appropriate word(s).
The storage capacity and format for each data type can be adjusted in the Field Property box
Indicate whether the statement is true or false
Which of the following states have a data breach notification law that mandates the notice contain the approximate date of the breach?
A. Massachusetts B. California C. Oregon D. New York