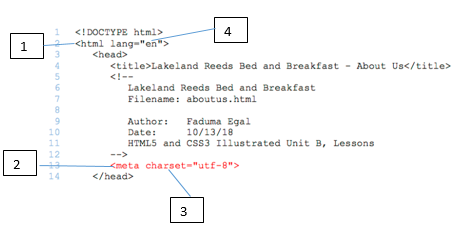
 ?
?
?
In the figure above, item ____ points to an attribute name.
A. 1
B. 2
C. 3
D. 4
Answer: C
Computer Science & Information Technology
You might also like to view...
Data produced by a computer is sent to a(n) ____________, which formats and presents it.
a. input device b. output device c. storage device d. program
Computer Science & Information Technology
If you wish to monitor logon failures, what should you do?
What will be an ideal response?
Computer Science & Information Technology
A structured collection of related information about people, events, and things
A) Database object B) Database management system C) Database
Computer Science & Information Technology
The internal vulnerability assessment is usually performed against every device that is exposed to the Internet, using every possible penetration testing approach. __________
Answer the following statement true (T) or false (F)
Computer Science & Information Technology