The ____________, __________ and ____________ are the only three forms of control necessary.
a. switch, if, else.
b. sequence, selection, iteration.
c. break, continue, if…else.
d. for, while, do…while.
b. sequence, selection, iteration.
You might also like to view...
A ________ is the smallest unit of digital information
A) bit B) byte C) character D) binary code
Enhance the Cafeteria Survey application from Tutorial 16 so that it draws a bar for each rating instead of asterisks. The user should still be able to choose ratings from a JComboBox and press a JButton to enter the selected rating. As ratings are input by the user, a horizontal bar graph appears in the JPanel as seen in Fig. 20.35. When 20 ratings have been entered, disable the Submit Rating JBut- ton.
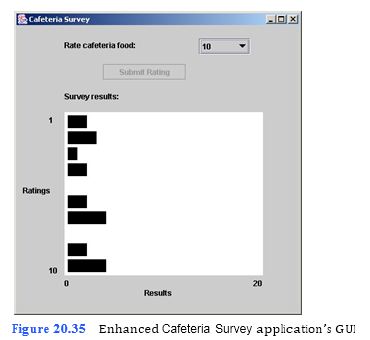
a) Copying the template to your working directory. Copy the C:Examples Tutorial20ExercisesEnhancedCafeteriaSurvey directory to your C:Simply- Java directory.
b) Opening the DrawJPanel template file. Open the template file DrawJPanel.java in your text editor.
c) Initializing variables. Inside the drawGraph method, before the repaint method call, declare two new int variables x and y, and initialize them to the value 5. Then, declare a new int variable width, but do not initialize it. The value of width will depend on the number of responses for each number. Declare a fourth int variable, height, which will be initialized to 20.
d) Creating a new MyRectangle object. After the declaration of the four int variables that you added in Step c, create a new MyRectangle object and assign it to variable bar.
e) Looping through the responses. After the declaration you added in Step d, begin a for statement that loops from 1 to 10, incrementing by one each time through the
Match each item with a statement below.
A. A more sophisticated device used in an office setting instead of a wireless router B. An attack that sends unsolicited messages to Bluetooth-enabled devices C. An attack that accesses unauthorized information from a wireless device through a Bluetooth connection D. An AP or another computer that is set up by an attacker designed to mimic the authorized Wi-Fi device E. Removing the built-in limitations and protections on Google Android devices F. Downloading an app from an unofficial third-party website G. A new class of mobile technology consisting of devices that can be worn by the user instead of carried H. A security setting that provides the optimum level of wireless security I. The technical name for a Wi-Fi network
A(n) ________ is a specific item of data located within a table
Fill in the blank(s) with correct word