FIGURE 13-1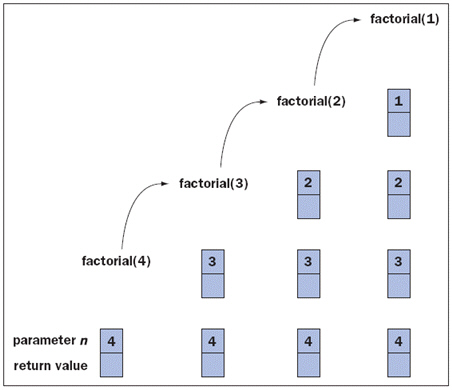 Figure 13-1 above shows an example of ____.
Figure 13-1 above shows an example of ____.
A. the trace of an iterative method
B. a big-O notation
C. activation records on the call stack
D. infinite recursion
Answer: C
You might also like to view...
The only state in which a thread has obtained the GIL is the________state.
a) born. b) ready. c) running. d) None of the above.
Which of the following statements are correct?
``` I: File file = new File("input.txt"); try (Scanner input = new Scanner(file)) { String line = input.nextLine(); } II: try (File file = new File("input.txt"); Scanner input = new Scanner(file);) { String line = input.nextLine(); } III: File file; try (file = new File("input.txt"); Scanner input = new Scanner(file);) { String line = input.nextLine(); } IV: File file; Scanner input; try (file = new File("input.txt"); input = new Scanner(file);) { String line = input.nextLine(); }``` a. I b. II c. III d. IV
The ____ keyword makes any specified properties or methods available throughout the program.
A. public B. private C. protected D. closed
What layer of the OSI model encapsulates data into frames?
A) Data link B) Physical C) Session D) Application