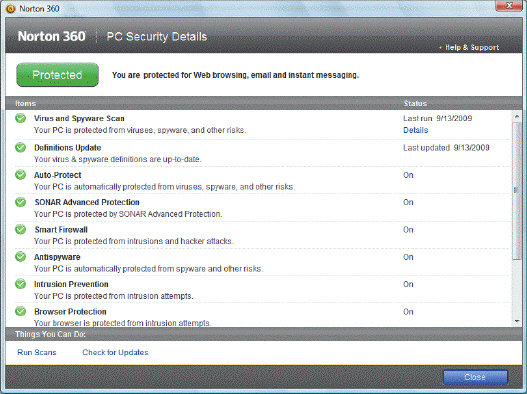
 The application shown in the accompanying figure is an example of a(n) ____.
The application shown in the accompanying figure is an example of a(n) ____.
A. firewall
B. Trojan horse
C. encryption program
D. security suite
Answer: D
Computer Science & Information Technology
You might also like to view...
Discuss what the process of vendor evaluation should focus on.
What will be an ideal response?
Computer Science & Information Technology
When you copy a formula from one cell to another, Excel automatically adjusts the cell references in the copied formula to reflect the new formula location.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
The Lookup ________ creates the menu of predefined values (lookup fields) by asking you questions and using your answers to create the options list.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
In order to change the background color for the application, you could set the BackColor property of the form.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology