When fraudulent sellers bid on the seller's items to drive up the price, it is called bid shielding
Indicate whether the statement is true or false.
False—This describes shill bidding.
You might also like to view...
What standard's implementation is built around periodic assessments of risk and feedback obtained during preventive maintenance inspections of the effectiveness of each control?
A. NIST 800-53 B. FIPS 200 C. FIPS 199 D. HIPAA
Which of the following statements describes a solution that solves this problem for Cloud Service Consumer A by improving both Cloud A and Cloud B environments?
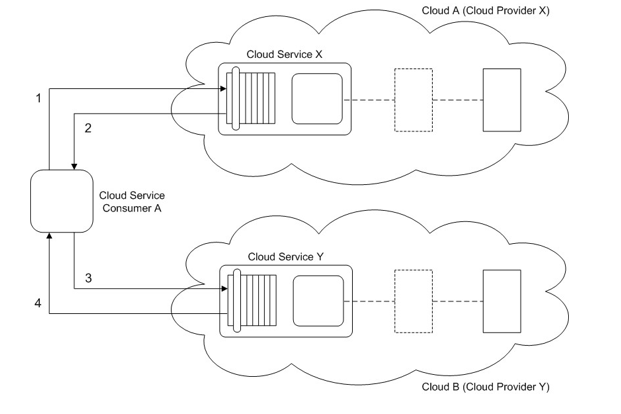
Cloud Service Consumer A accesses Cloud Service X (1) that resides in Cloud A. Cloud Service X processes the request from Cloud Service Consumer A and then sends back a response with the requested data (2). Cloud Service Consumer A then sends a message to Cloud Service Y (3) that resides in Cloud B. The message contains some of the data received from Cloud Service X. After processing the request, Cloud Service Y sends back a response with a success or failure code (4).
Cloud A is a private cloud owned by the same organization that owns Cloud Service Consumer A. Cloud B is a community cloud owned by a group of organizations. The availability rating of Cloud Service X, as indicated in its SLA, is 99.98%. When Cloud Service Consumer A issues a request message to Cloud Service X, it can result in prolonged processes as Cloud Service X attempts to gather the requested data from various data sources. Because Cloud Service X is shared by other cloud service consumers and because the data sources are also shared by other parts of the o
You have decided to change the instance type for instances running in your application tier that is using Auto Scaling. In which area below would you change the instance type definition?
A. Auto Scaling policy B. Auto Scaling group C. Auto Scaling tags D. Auto Scaling launch configuration
Briefly define caps.
What will be an ideal response?