The Chief Information Security Officer (CISO) is concerned that users could bring their personal laptops to work and plug them directly into the network port under their desk. Which of the following should be configured on the network switch to prevent this from happening?
A. Access control lists
B. Loop protection
C. Firewall rule
D. Port security
Answer: D. Port security
You might also like to view...
Which of the following choices is part of the IEEE 1016 standard's 12 views, and is used to document the internal functions and organization of a software item?
A. Structure B. Interaction C. State dynamics D. Resource
Configure the spanning tree cost on SW3 to prefer the FastEthernet 0/1.
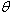
What will be an ideal response?
A(n) ________ query is used to display aggregate data in a row-and-column layout
A) crosstab B) action C) summary D) outline
____________________ is the process in which a single large network is subdivided into several smaller networks to control traffic flow and improve manageability.
Fill in the blank(s) with the appropriate word(s).