Digital signatures are designed to address ________.
a) privacy
b) authorization
c) authentication
d) nonrepudiation
c) authentication
You might also like to view...
Answer, and explain: For large lists, deleting an item from a linked list compared to deletion from an array is
a) more efficient. b) less efficient. c) about the same. d) depends on the size of the two lists.
____ modes define how an object interacts with other objects, specifically with respect to tonal adjustments.
a. Default b. Threshold c. Shading d. Blending
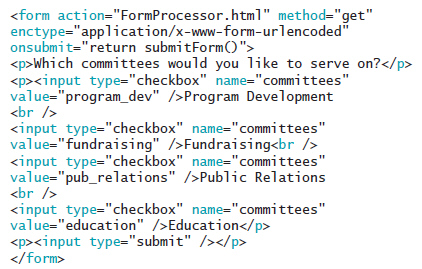 To get a reference to the first check box in the form seen in the accompanying figure, use the statement ____.
To get a reference to the first check box in the form seen in the accompanying figure, use the statement ____.
A. document.getElementById("check box"); B. document.getElementsByName("committees")[1]; C. document.getElementsByName("committees")[0]; D. document.getElementById("program_dev");
Design Mode must be turned on in order to protect a document.
Answer the following statement true (T) or false (F)