The ________ function is used with the IsNull function to decide what to display if a formula is referencing a null value
Fill in the blank(s) with correct word
IIF
Computer Science & Information Technology
You might also like to view...
The most promising approach to improved password security is __________ . ??
A. user education ?? B. a proactive password checker C. computer generated passwords D. a reactive password checking strategy
Computer Science & Information Technology
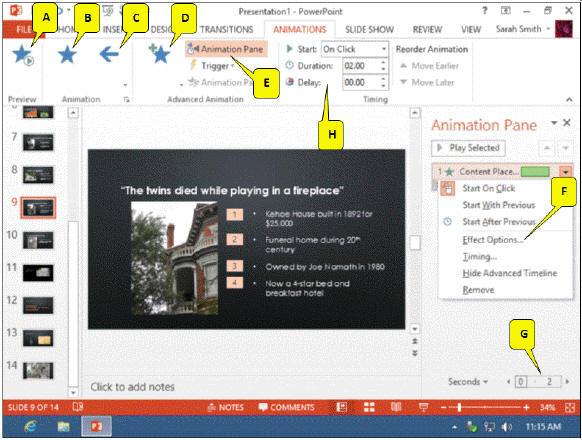 Referring to the accompanying figure, which callout points to the option used to customize the animation?
Referring to the accompanying figure, which callout points to the option used to customize the animation?
A. D B. E C. F D. G
Computer Science & Information Technology
The project calendar is also called the ____________________ calendar.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Security awareness and training and workforce security standards are examples of which of the following?
A. Administrative safeguards B. Physical safeguards C. Technical safeguards D. Organizational requirements
Computer Science & Information Technology