When securing a database the user must be careful to ensure that the database is protected adequately
Indicate whether the statement is true or false
FALSE
You might also like to view...
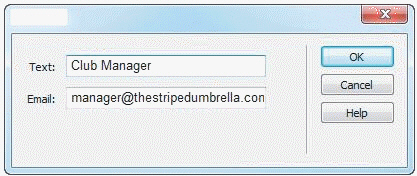 In the accompanying figure, the topmost text box is the ____ for the e-mail link on a web page.
In the accompanying figure, the topmost text box is the ____ for the e-mail link on a web page.
A. link information B. banner C. text D. link
A ____ is a grouping of storage devices that forms a subnet.
A. Local Area Network (LAN) B. Wide Area Network (WAN) C. Storage Area Network (SAN) D. System Area Network (SAN)
When viewing the pinout for T568B, what is the correct order of wire colors, starting at pin 1?
a. white/green, green, white/orange, blue, white/blue, orange, white/brown, brown b. blue, white/blue, green, white/green, orange, white/orange, brown, white/brown c. white/orange, orange, white/green, blue, white/blue, green, white/brown, brown d. white/brown, brown, white/green, blue, white/blue, green, orange, white/orange
In regard to programming, what is the purpose of the "Enable Look Ahead" checkbox entry in the Workstation Options window?
What will be an ideal response?