Explain the two points administrators should remember if they are wary of using the same tools that attackers use.
What will be an ideal response?
Administrators who are wary of using the same tools that attackers use should remember two important points: (1) Regardless of the nature of the tool used to validate or analyze a firewall's configuration, it is the intent of the user that dictates how the information gathered will be used, and (2) In order to defend a computer or network, it is necessary to understand the ways it can be attacked. Thus, a tool that can help close up an open or poorly configured firewall helps the network defender minimize the risk from attack.
You might also like to view...
The day-one status of the data asset base is established through the ____.
A. reference evaluation B. standard evaluation C. remediation evaluation D. baseline status evaluation
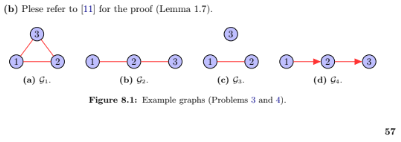
Consider graphs G 2 and G 3 shown in Figure 8.1. From the adjacency and Laplacian spectra of the graphs, what can be commented on the connectivity of the graphs?
How does the Action Center list messages?
A) In the order of severity-most severe to least B) In alphabetical order C) In date order-newest to oldest D) In date order-oldest to newest
_____ A database is a collection of information organized so that its contents can easily be accessed, managed, and updated
Indicate whether the statement is true or false