How can operational controls be used to improve security compliance?
A. Track activities with auditing and review the audit logs.
B. Implement encryption and multifactor authentication.
C. Set procedures for work tasks and provide training.
D. Require M-of-N controls and place administrators into compartmented areas.
Answer: C. Set procedures for work tasks and provide training.
You might also like to view...
Consider an unweighted and undirected wireless network, as shown in Figure 6.18 in the text book (reproduced as Figure 6.1 of this solution manual). Identify the nodes with the highest wireless flow betweenness. What are the impacts on the resources of the nodes with high WFB?
What will be an ideal response?
Picture ________ are picture styles that include bevels, 3-D rotations, and soft edges
Fill in the blank(s) with correct word
?In the accompanying figure of Microsoft Access 2016, Box A points to the _____.
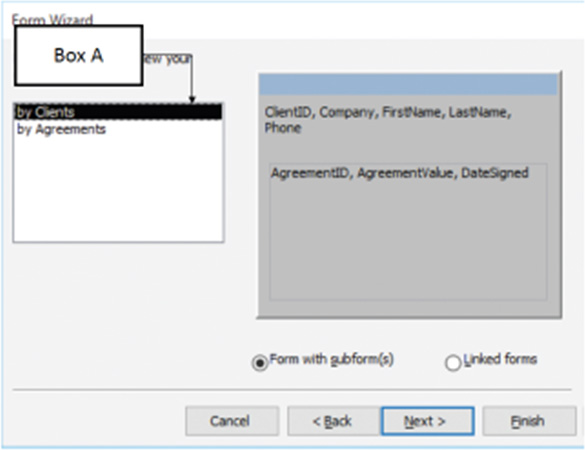
A. layout of data in linked form B. ?order in which data will be displayed C. ?data extracted from a main form D. title for the subform
Which symbol represents that a cell is an absolute cell reference in a function or formula?
A) % B) * C) $ D) &