A honeypot might be used in a network for which of the following reasons
a. Lure or entrap hackers so that law enforcement can be informed
b. Gather information on new attacks and threats
c. Distract hackers from attacking legitimate network resources
d. Protect the DMZ from internal attacks
Ans:
a. Lure or entrap hackers so that law enforcement can be informed
b. Gather information on new attacks and threats
c. Distract hackers from attacking legitimate network resources
You might also like to view...
What is a dispersion compensating fiber?
What will be an ideal response?
Modify the INSTALLED SOFTWARE TRANSACTION, which is used to update the SOFTWARE MASTER and to produce the SOFTWARE INSTALLATION LISTING. Delete the TITLE and VERSION NUMBER, because they may be obtained from the SOFTWARE MASTER and are redundant keying. Add the HARDWARE INVENTORY NUMBER, specifying the installation computer. Delete the CAMPUS LOCATION and ROOM LOCATION, because they are elements of the installation computer.
What will be an ideal response?
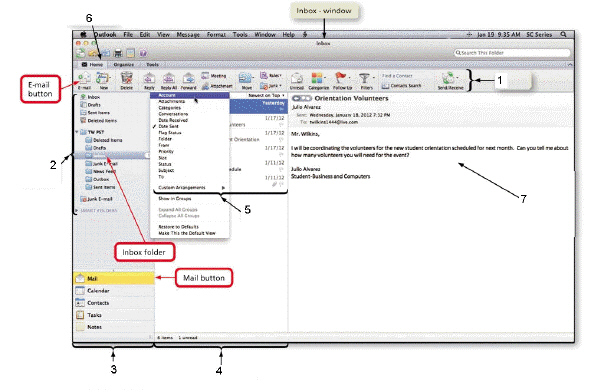 The item numbered 2 in the accompanying figure is the ____.
The item numbered 2 in the accompanying figure is the ____.
A. Mail folder pane B. Navigation Pane C. message pane D. Reading Pane
In ncurses YaST, you selected highlighted menu items by pressing the ____.
A. Tab key B. Shift key C. Arrow keys D. Spacebar