XPath 2.0 is fundamentally based on tokenized values, which are values that cannot be broken into smaller parts.
Answer the following statement true (T) or false (F)
False
You might also like to view...
The expression following the switch keyword is called a
a) guard condition b) controlling expression c) selection expression d) case expression
Referring to the figure below, please identify the letter of the choice that best matches the numbered area on the screen.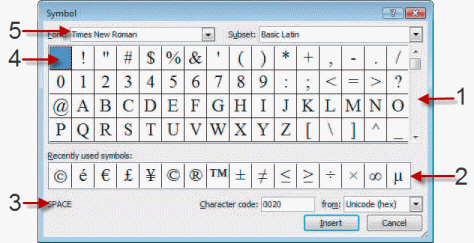
A. Scroll bar B. Recently used symbols C. Name of currently selected symbol D. Currently selected symbol E. Font list box
One of the first modern techniques added to firewalls is ____________________ inspection, or the capability to tell if a packet is part of an existing connection.
Fill in the blank(s) with the appropriate word(s).
An AIR app can be played without a(n) ____________________ .
Fill in the blank(s) with the appropriate word(s).