Given the doubly linked list in the diagram below, give the code to delete the second node in the list with the number 31. Assume each entry in the list is a node of class Node with a public next and prev member variable.
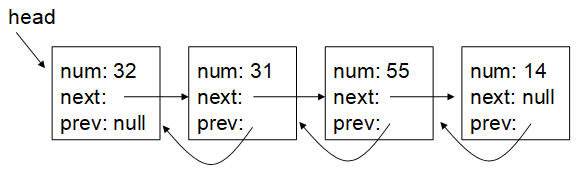
```
Node *toDelete = head->next;
head->next->next->prev = head;
head->next = toDelete->next;
delete toDelete;
```
You might also like to view...
A linked list class uses a Node class with successor reference next and field element to store values. A recursive method to print all list elements can be written as
A) static void printList(Node list) { if (list != null) { System.out.println(list.element); printList(list.next); } } B) static void printList(Node list) { while (list!= null) { System.out.println(list.element) printList(list.next); list = list.next; } } C) static void printList(Node list) { while (list.next != null) { printList(list.next); System.out.println(list.element) list ++; } } D) static void printList(Node list) { System.out.println(list.element): printList(list.next); }
The terms "vulnerable" and "least advantaged" are synonyms.
Answer the following statement true (T) or false (F)
The first step in evaluating access is to determine if access permission is enabled at the VPN (or dial-up RAS) server.
Answer the following statement true (T) or false (F)
Explain several reasons for segmenting networks.
What will be an ideal response?