Which of the following processes is one method of obtaining a list of the active hosts on a network?
A. ICMP query
B. query
C. IP address scanning
D. firewalking
Answer: C
You might also like to view...
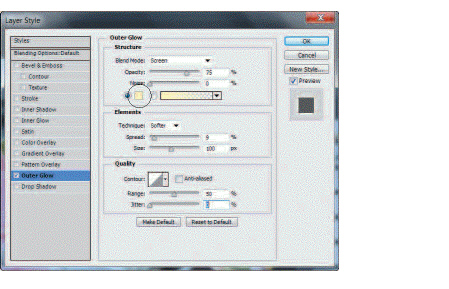 In the accompanying figure, the circled item is the ____ square.
In the accompanying figure, the circled item is the ____ square.
A. Opacity level B. Set color of glow C. Structure style D. Blend mode color
Case-Based Critical Thinking QuestionsCase 2-2Henry knows that the Free Transform tool is very powerful but he has some questions about its use, so he drops by his neighbor Steve's house to get some tips. With a quick click of the mouse, Steve now has a bounding box with points and tangent handles that Henry can adjust to warp the umbrella. What modifier is he using?
A. Bounding Box B. Tangent C. Envelope D. Rotate and Skew
You can click the Logical button (Formulas tab | Function Library group) and click IFERROR to insert the IF function.
Answer the following statement true (T) or false (F)
You do not have to use a reference for a source used from Twitter, YouTube or Television in APA or any other citation style.
Indicate whether the statement is true or false.