Access reports present data in a way that is optimized for:
A) printing.
B) social media.
C) texting.
D) compatibility.
A
You might also like to view...
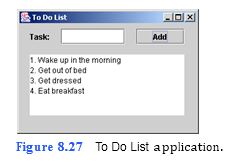
(To-Do List Application) Use a JTextArea as a to-do list. Enter each item in a JTextField, and add it to the JTextArea by clicking a JButton. The item should be displayed in a numbered list as in Fig. 8.27. To do this, you will need JTextArea method getLineCount, which returns the number of lines in a JTextArea. The following statement assigns the number of lines displayed in the outputJTextArea to int variable counter: getLineCount, which returns the number of lines in a JTextArea. The following statement assigns the number of lines displayed in the outputJTextArea to int variable counter:
```
int counter = outputJTextArea.getLineCount();
```
```
a) Copying the template to your working directory. Copy the directory C:Examples Tutorial08ExercisesToDoList to your C:SimplyJava directory.
b) Opening the template file. Open the ToDoList.java file in your text editor.
c) Adding code to the event handler for the Add JButton. Add code to the addJBut- tonActionPerformed event handler (which begins in line 82) to obtain the number of lines displayed in the outputJTextArea. Get the user input from taskJText- Field append it the outputJTextArea with a line number in front of it. After the input is added to the outputJTextArea, clear the taskJTextField.
d) Saving the application. Save your modified source code file.
e) Opening the Command Prompt window and changing directories. Open the Command Prompt window by selecting Start > Programs > Accessories > Command Prompt. Change to your working directory by typing cd C:SimplyJavaToDoList.
```
Text boxes automatically ________ to fit the text as you type
Fill in the blank(s) with correct word
Explain the difference between a pretest loop and a posttest loop.
What will be an ideal response?
Which of the following is not true about the message to enable editing or enable content?
a. You might encounter these security features if you open a file from an e-mail or download files from the Internet. b. In Office 2010, some files open in Private View if the file appears to be from a potentially risky location, such as the Internet. c. These options are new security features in Office 2010 that protect your computer from malicious files by opening them in a restricted environment until you enable them. d. Trusted Documents is another security feature that remembers which files you have already enabled.