An encryption virus replicates itself onto a hard drive's master boot record
Indicate whether the statement is true or false
FALSE
You might also like to view...
A subclass can directly access __________.
a. only protected and private members of the superclass b. all members of the superclass c. only public and private members of the superclass d. only public and protected members of the superclass
Wireless sensors are most effective when their ____ overlap.
A. thresholds B. signatures C. footprints D. keys
Office 2016 is designed for the _________________________, which means you can access the Office work you create from any device, as long as they are connected to the Internet.
Fill in the blank(s) with the appropriate word(s).
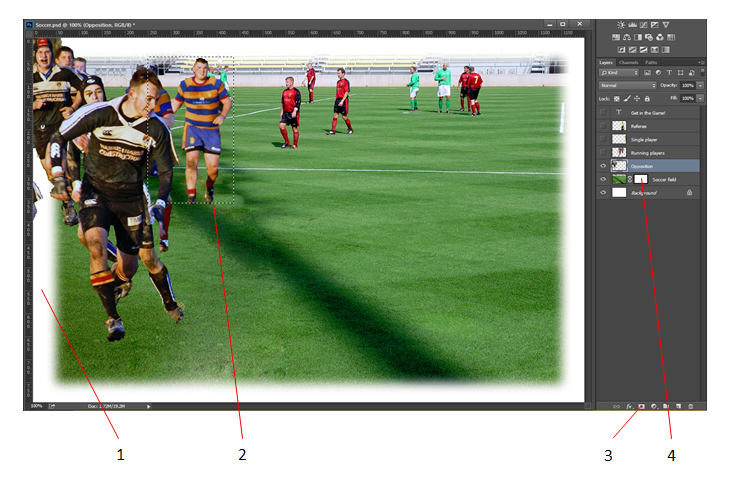
A. Show Thumbnails B. Default Foreground and Background C. Delete Mask D. Add a Layer Mask