Setting up equipment to spoof a carrier?s tower and infrastructure is known as _______________.
A. network ghosting
B. cell tower control
C. network analysis
D. tower spoofing
Answer: D
Computer Science & Information Technology
You might also like to view...
Which one of the following statements initializes a variable with an integer literal?
a. int score = 2500; b. decimal total = 156.78m; c. double rate = 0.00435; d. string name = "Michelle";
Computer Science & Information Technology
_________ involves counting the number of occurrences of a specific event type over an interval of time. ?
A) ?Rule-based detection ? ? B) ?Resource usage C) ?Threshold detection ? D) ?Profile-based system
Computer Science & Information Technology
In C++, the default precision is set to ____ decimal places.
a. five b. six c. seven d. eight
Computer Science & Information Technology
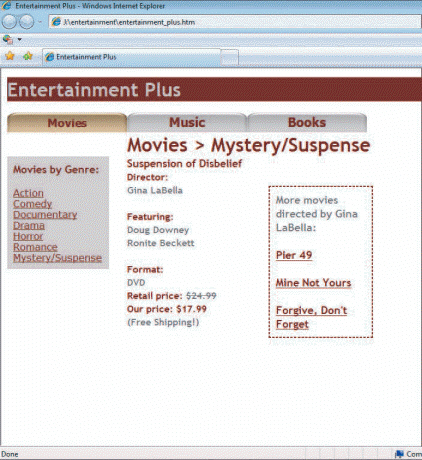 In the figure above, the tabs at the top that say "Movies," "Music," and "Books" are examples of ____ navigation.
In the figure above, the tabs at the top that say "Movies," "Music," and "Books" are examples of ____ navigation.
A. Global B. Local C. Related D. Tabbed
Computer Science & Information Technology