FIGURE 12-2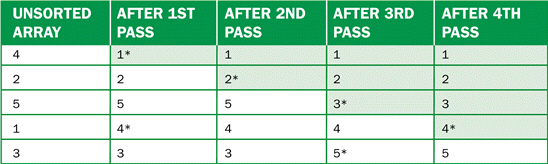 Figure 12-2 above shows an example of a trace of data during a(n) ____ sort.
Figure 12-2 above shows an example of a trace of data during a(n) ____ sort.
A. insertion
B. bubble
C. linear
D. selection
Answer: D
You might also like to view...
After you cut, _____.
A. the text is not removed from its original location and placed on the Clipboard B. the text is removed from its original location and placed on the Clipboard C. the text is removed from its original location and saved in the file D. the text is removed from its original location and placed on the desktop
____ is a defect where the edges, especially the corners, of an image are darker than the center.
a. Chromatic Aberration b. Angle Error c. Vignette distortion d. Pincushion Distortion
For key values of 84 and 108 and a hashing function of key % 12, what is the result?
A. indexes of 7 and 9 B. indexes of 0 and 1 C. a collision D. indexes of 12 and 14
Each packet/datagram contains a source port and destination port.
Answer the following statement true (T) or false (F)