Acme Widgets recently experienced an attack in which the attacker broke into a file server and stole product plans. Which of the following is a goal of information security that was violated?
What will be an ideal response?
Confidentiality
Computer Science & Information Technology
You might also like to view...
__________ is not an example of a network transmission medium.
a) Water b) Copper wiring c) Optical fiber d) Air
Computer Science & Information Technology
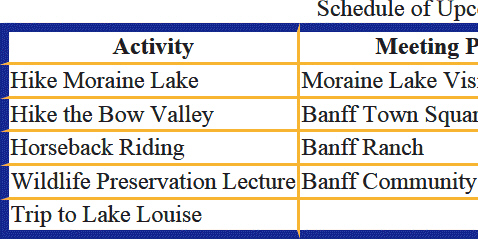 As shown in the accompanying figure, a(n) ____________________ is a horizontal group of cells.
As shown in the accompanying figure, a(n) ____________________ is a horizontal group of cells.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The number of bits processed at one time is the processor's
A) Letter size B) Word size C) Paragraph size D) Page size
Computer Science & Information Technology
BitLocker uses the __________to provide secure protection of encryption keys and checking of key components when Windows is booting
a. Trusted Platform Module b. USB port c. NTFS file system d. None of the above
Computer Science & Information Technology