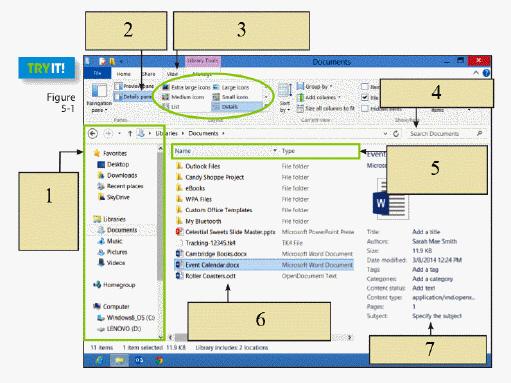
 In the figure above, item 1 is pointing to the ____.
In the figure above, item 1 is pointing to the ____.
A. file list displaying subfolders and files for the item
B. Navigation pane
C. column headings
D. details pane
Answer: B
You might also like to view...
Write a code fragment that prints every other character in a String object called word starting with the first character.
What will be an ideal response?
The break command provides the ability to ____.
A. Terminate the execution of a loop at any time. B. Temporarily pause script execution C. Place a script in debug mode D. None of the above
Which of the following is NOT a part of system hardening?
A. Unnecessary applications should be removed. B. All services should be enabled. C. Unrequired ports should be blocked. D. External storage devices and media should be tightly controlled.
Answer the following statements true (T) or false (F)
1. Buffer overflow attacks are one of the most common attacks seen. 2. Buffer overflow exploits are no longer a major source of concern to security practitioners. 3. A buffer overflow error is not likely to lead to eventual program termination. 4. To exploit any type of buffer overflow the attacker needs to identify a buffer overflow vulnerability in some program that can be triggered using externally sourced data under the attackers control. 5. At the basic machine level, all of the data manipulated by machine instructions executed by the computer processor are stored in either the processor’s registers or in memory.