Which of the following is the BEST example of social engineering?
A. A caller pretending to be an administrator to acquire a password
B. A social website that secretly records users actions on the Internet
C. A program that attempts to steal users credit card information
D. An unsolicited email that attempts to get a user to make a purchase
Answer: A. A caller pretending to be an administrator to acquire a password
You might also like to view...
Which of the following is not an STL container type?
a. Second-class containers. b. Sequence containers. c. Associative containers. d. Container adapters.
If you are developing a Web site for a client, this is the time to conduct a user analysis. Describe the general characteristics of your users including learning style, knowledge of technology, age, and general education level. If this Web site supports an office function, describe workers’ knowledge about their jobs. Will the site have secondary users as well as primary users? Also specify their level of familiarity with your Web site. Cite the sources of your information.
What will be an ideal response?
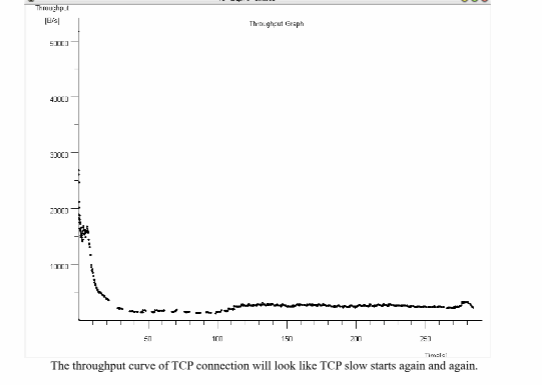
Generate a Throughput Graph to view the data rate of the TCP connection. How does the throughput change after the flood of pings is started?
A technician is setting up a firewall on the network that would show a public IP address out to the Internet and assign private IP addresses to users inside the network. Which of the following processes should be set up?
A. Port security B. MAC filtering C. ACL D. NAT