The item marked 3 in the accompanying figure is the ____ Tool.
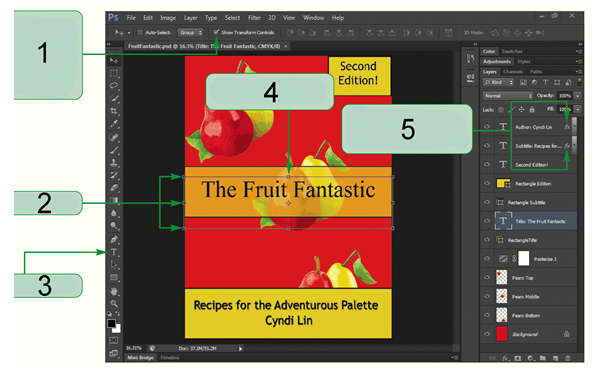
a. Pen
b. Horizontal Type
c. Selection
d. Outline
B. Horizontal Type
Computer Science & Information Technology
You might also like to view...
Every Java application is composed of at least one:
a. local variable b. instance variable c. public class declaration d. imported class
Computer Science & Information Technology
Tabular data formatted as ________ can be converted into columns using the Convert Text to Columns Wizard
A) comma-separated values B) special characters C) delimiters D) metadata
Computer Science & Information Technology
Micro blocks, SYN cookies, RST cookies, and stack tweaking are defenses against ______
a. TCP SYN flood attacks b. Phishing c. Viruses d. None of the above
Computer Science & Information Technology
The most difficult type of malware to detect and remove is adware
a. true b. false
Computer Science & Information Technology