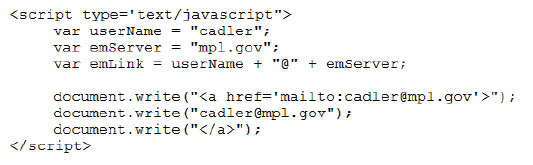
 In the figure above, what are the variables?
In the figure above, what are the variables?
A. userName
B. emServer
C. emLink
D. all the above
Answer: D
You might also like to view...
You should use the for statement to generate repetitive flow behavior when you do not know in advance the number of repetitions required.
Answer the following statement true (T) or false (F)
Queue nodes are removed only from the_______ of the queue and are inserted only at the_______ of the queue.
a) tail, head. b) head, tail. c) top, top. d) None of the above.
Which of the following is the goal of an Integrity Controls standard?
A) Implementing technical controls that protect ePHI from improper alteration or destruction B) Restricting access to ePHI only to users and processes that have been specifically authorized C) Implementing hardware, software, and procedural mechanisms that record and examine activity in information systems that contain ePHI D) Verification that a person or process seeking to access ePHI is the one claimed
How is the IT part of an organization involved with the regulations defined by FERPA, FISMA, GLBA, HIPAA, and PCI DSS?
What will be an ideal response?