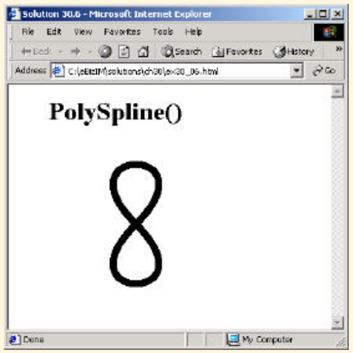
Look up the Spline method mentioned in the documentation at the URL provided in Section 30.1, and use it to create a figure-eight shape.
What will be an ideal response?
```
1
2
3
4
5
6
7
8
9
10
11
12 PolySpline()
13
14
17 CLASSID = "CLSID:369303C2-D7AC-11d0-89D5-00A0C90833E6">
18
19
20
21
23
24
25
26
```
You might also like to view...
Match the following grouping button with the corresponding description:
I. 1 II. 2 III. 3 IV. 4 V. + A. Collapse outline to display the grand total only. B. Displays subtotals by the main subtotal category, the secondary subtotal category, and the grand total. C. Expand an outline group to see its details. D. Display the entire list. E. Display subtotals by the main subtotal category and the grand total.
Identify the three most probable threats to a computing system in an office with fewer than 10 employees. That is, identify the three vulnerabilities most likely to be exploited. Estimate the number of times each vulnerability is exploited per year. Justify your estimate
What will be an ideal response?
If we store the address of grade[0] in a pointer named gPtr (using the assignment statement gPtr = &grade[0];), then, the expression ____ references grade[0].
A. gPtr(0) B. gPtr C. &gPtr D. *gPtr
Clicking the _______________ checkbox for a particular NTFS permission tells Windows to overrule inheritance and stop that particular NTFS permission.
Fill in the blank(s) with the appropriate word(s).