?Information (contained on the devices) is protected by three layers: products, ____, and policies and procedures.
a. people
b. systems
c. applications
d. tools
Answer: a. people
Computer Science & Information Technology
You might also like to view...
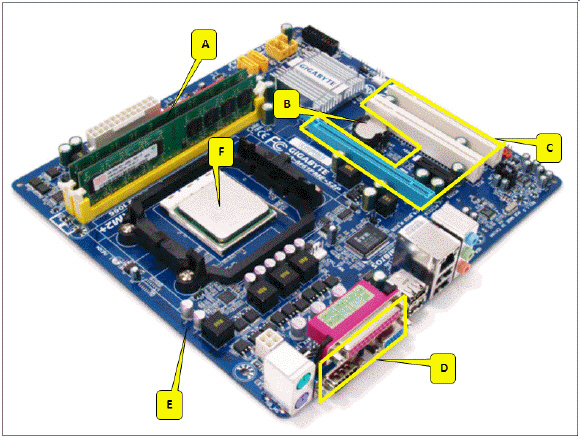 Referring to the accompanying figure, which of the following callouts points to the slots for expansion cards?
Referring to the accompanying figure, which of the following callouts points to the slots for expansion cards?
A. D B. C C. B D. A
Computer Science & Information Technology
This type of MAC filtering provides the best option for security and management.
a. whitelist b. graylist c. blacklist
Computer Science & Information Technology
A company is experiencing accessibility issues reaching services on a cloud-based system. Which of the following monitoring tools should be used to locate possible outages?
A. Network analyzer B. Packet analyzer C. Protocol analyzer D. Network sniffer
Computer Science & Information Technology
The binary number 10110100 has what decimal equivalent?
a. 114 b. 190 c. 172 d. 180
Computer Science & Information Technology