FIGURE 10-1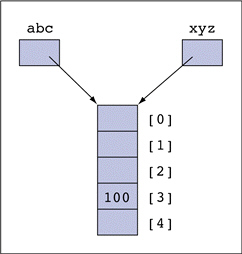 Figure 10-1 above shows ____.
Figure 10-1 above shows ____.
A. two values referring to the same array variable
B. an array with two strings of values
C. an array with two names
D. two variables referring to the same array object
Answer: D
You might also like to view...
Charts can help you to communicate information to your audience. Please explain how you can add a bar, line, or pie chart to your presentation, how to change the sample data in a chart, and how to delete sample data.
What will be an ideal response?
How does the use of a SecureSessionModule prevent session high jacking attacks?
A. It validates all input. B. It modifies each session ID by appending a hash to the ID. C. It encrypts the session ID. D. t prevents the embedding of a site within a frame.
You cannot undo updates or deletions performed by a(n) ________ query.
Fill in the blank(s) with the appropriate word(s).
A ___________ makes use of both signature and anomaly detection techniques to identify attacks.
Fill in the blank(s) with the appropriate word(s).