Discuss and explain the various types of malicious code and how they work. Include the different types of viruses
What will be an ideal response?
Malicious code includes a variety of threats such as viruses, worms, Trojan horses, ransomware, and bot programs. A virus is a computer program that can replicate or make copies of itself and spread to other files. Viruses can range in severity from simple programs that display a message or graphic as a "joke" to more malevolent code that will destroy files or reformat the hard drive of a computer, causing programs to run incorrectly. Worms are designed to spread not only from file to file but from computer to computer and do not necessarily need to be activated in order to replicate. A Trojan horse is not itself a virus because it does not replicate but it is a method by which viruses or other malicious code can be introduced into a computer system. It appears benign and then suddenly does something harmful. For example, it may appear to be only a game and then it will steal passwords and mail them to another person. A backdoor is a feature of worms, viruses, and Trojans that allow attackers to remotely access compromised computers. Ransomware (or also known as scareware) is a type of malware (often a worm) that locks your computer or files to stop you from accessing them. Bot programs are a type of malicious code that can be covertly installed on a computer when it is attached to the Internet. Once installed, the bot responds to external commands sent by the attacker, and many bots can be coordinated by a hacker into a botnet.
You might also like to view...
The Modified Internal rate of Return (MIRR) in cell B9 will be ___________ the Internal Rate of Return (IRR) in B8.
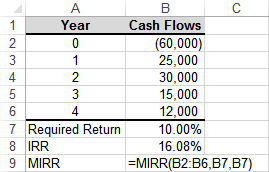
a) less than
b) equal to
c) greater than
d) Could be any of the above
e) None of the above
Which of the following is not a major difficulty in conducting a retail audit?
a. An audit may be very time-consuming. b. An audit may be quite costly. c. A yearly audit may be much too frequent. d. Employees may feel threatened and not fully cooperate.
The best table and seating option to promote informality and intimacy in mediation is a square or rectangular table with the parties sitting at adjacent sides or 90-degree angles
Indicate whether the statement is true or false.
The basic premise of unrelated diversification is that
A. the best companies to acquire are those that offer the greatest economies of scope rather than the greatest economies of scale. B. any company that can be acquired on good financial terms and that has satisfactory growth and earnings potential represents a good acquisition and a good business opportunity. C. the task of building shareholder value is better served by seeking to stabilize earnings across the entire business cycle than by seeking to capture cross-business strategic fits. D. the best way to build shareholder value is to acquire businesses with strong cross-business financial fit. E. the least risky way to diversify is to seek out businesses that are leaders in their respective industry.