A disadvantage of single-point anonymizers is that they use arms-length communication that protects IP address and related identifying information.
a. true
b. false
Answer: b. false
Computer Science & Information Technology
You might also like to view...
In which form of authentication does the authenticating device generate a random code and send it to the user who wants to be authenticated?
A. basic B. challenge/response C. biometrics D. signature
Computer Science & Information Technology
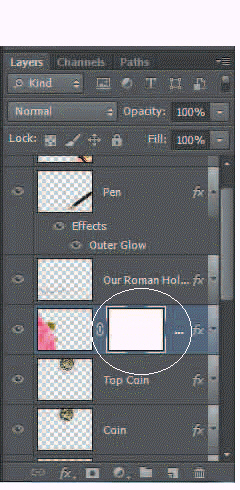 If there were a red X in the area indicated by the line in the accompanying figure, it would mean that the ____________________ is inactive.
If there were a red X in the area indicated by the line in the accompanying figure, it would mean that the ____________________ is inactive.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Table style options include separate formatting settings for row and column headers, alternate rows or columns, and summary rows or columns
Indicate whether the statement is true or false
Computer Science & Information Technology
When inserting a footnote in a document, you need to type the footnote number
Indicate whether the statement is true or false
Computer Science & Information Technology