Which IPv6 ACL statement would be used to allow all TFTP traffic coming from the 2001:db8:5d21:b232::/64 network to the 2001:db8:e456:db34::/64 network?
A) permit udp 2001:db8:5d21:b232::/64 2001:db8:e456:db34::/64 eq 69
B) allow udp 2001:db8:5d21:b232::/64 2001:db8:e456:db34::/64 eq 54
C) permit tcp 2001:db8:5d21:b232::/64 2001:db8:e456:db34::/64 eq 54
D) allow tcp 2001:db8:5d21:b232::/64 2001:db8:e456:db34::/64 eq 69
A
Explanation: A) The permit {ipv6 | tcp | udp} {source-ipv6-prefix/prefix-length | any | host source-ipv6-address} [operator port-number] {destination-ipv6-prefix/prefix-length | any | host destination-ipv6-address} [operator port-number] command is used when configuring extended IPv6 ACLs. To allow all TFTP traffic from the 2001:db8:2525:6342::/64 network to the 2001:db8:3672:2643::/64 network, the permit udp 2001:db8:5d21:b232::/64 2001:db8:e456:db34::/64 eq 69 statement would be used.
You might also like to view...
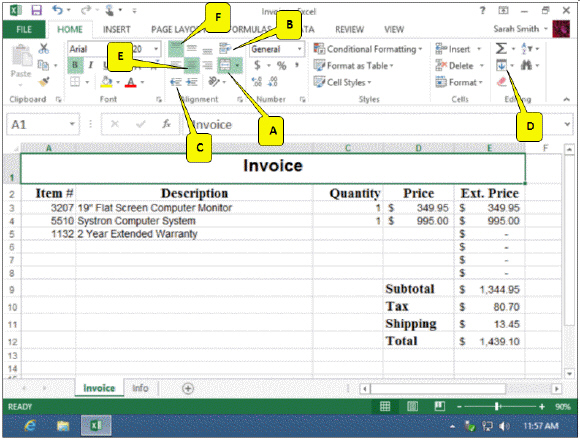 In the accompanying figure, which callout points to the Merge and Center button?
In the accompanying figure, which callout points to the Merge and Center button?
A. A B. B C. C D. D
How does the computer keep track of all the calls to a recursive function?
What will be an ideal response?
The ________ function is used to find the median of values in a range
A) SUM B) AVERAGE C) COUNT D) COUNTA
In public key cryptography, the ____ key encrypts the message.
A. public B. private C. known D. user