What is one way a hacker can steal the software that makes up the application?
A. Unauthorized access to directories
B. steal data packets
C. ARP attacks
D. Denial of Service
Answer: A
You might also like to view...
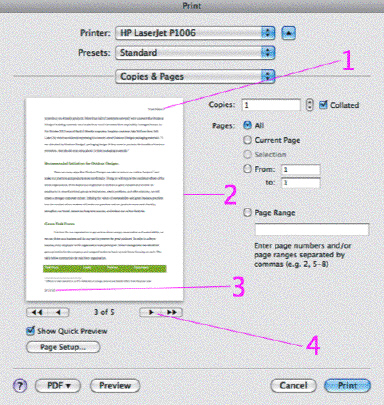 In the accompanying figure, Item 3 points to the ____.
In the accompanying figure, Item 3 points to the ____.
A. footer B. header C. citation D. footnote
_____ is a protocol for securely accessing a remote computer.
A. Transport Layer Security (TLS) B. Secure Shell (SSH) C. Secure Sockets Layer (SSL) D. Secure Hypertext Transport Protocol (SHTTP)
A buffer _________ is a condition at an interface under which more input can be placed into a buffer or data holding area than the capacity allocated, overwriting other information.
A. overflow B. overrun C. overwrite D. all the above
____ is a set of Perl modules that provide a simple and consistent Application Programming Interface (API) to the World Wide Web.
A. Crypt::Web:Lib B. RC4 C. Crypt::Lib:Web D. LWP