List the significant guidelines used in the formulation of effective information security policy.
What will be an ideal response?
For policies to be effective, they must be properly:1. Developed using industry-accepted practices2. Distributed or disseminated using all appropriate methods3. Reviewed or read by all employees4. Understood by all employees5. Formally agreed to by act or assertion6. Uniformly applied and enforced
You might also like to view...
The ________ abstract classes are Unicode character-based streams.
a. Reader and Writer b. BufferedReader and BufferedWriter c. CharArrayReader and CharArrayWriter d. UnicodeReader and UnicodeWriter
The hypertext markup language (HTML) documents that you create using Word can be viewed in what type of program?
What will be an ideal response?
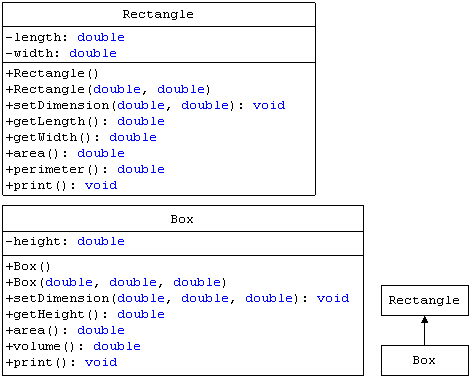 Based on the diagram in the accompanying figure, the method area in the class Box ____ the method area in the class Rectangle.
Based on the diagram in the accompanying figure, the method area in the class Box ____ the method area in the class Rectangle.
A. overloads B. overrides C. overstates D. deletes
Which of the following integrates MRP II with the information flow across an organization to manage and coordinate the ongoing activities of the enterprise?
A. Enterprise Resource Production B. Excellent Customer Production C. ?Enterprise Resource Pplanning D. ?Enterprise Customer Planning