A system can be considered completely secure once it passes an IT audit.
a. true
b. false
b. false
Computer Science & Information Technology
You might also like to view...
Mac users can set up their computers to run both Windows and Mac OS X and select the platform they want to work with when they boot their computers. This is called dual ______.?
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The markers for changing the column width will only appear if your cursor is somewhere in the table
Indicate whether the statement is true or false
Computer Science & Information Technology
The \s character is used in a regular expression to set up a match based on white space.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
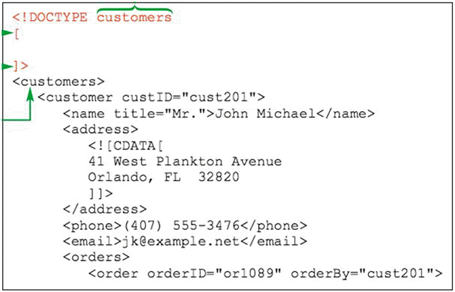
Answer the following statement true (T) or false (F)
Computer Science & Information Technology