The conflict between the users' goal for unfettered access to data and the security administrator's goal to protect that data is an issue of ______________
a. System administration
b. Access control
c. Password protection
d. Social engineering
Answer B.
Computer Science & Information Technology
You might also like to view...
What are the most common types of equipment that are used to establish broadband connections to ISPs?
What will be an ideal response?
Computer Science & Information Technology
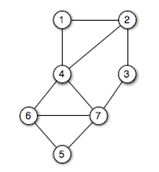
List all of the cycles in the graph below.
Computer Science & Information Technology
________, invented in 1947, led to second-generation computers in the 1950s and 1960s
A) The central processing unit B) Transistors C) Vacuum tubes D) Integrated circuits
Computer Science & Information Technology
The ________ tool enables you to find Wiki articles and related searches from the web
Fill in the blank(s) with correct word
Computer Science & Information Technology