What Precautions are used to protect the computer network from both internal and external Web security threats?
What will be an ideal response?
What Precautions are used to protect the computer network from both internal and external Web security threats?
You might also like to view...
The kernel ensures that the value of a semaphore will
A. never be negative B. never exceed a certain value
(Drawing Patterns with Nested for Loops) Write a program that uses for statements to print the following patterns separately, one below the other. Use for loops to generate the patterns. All asterisks (*) should be printed by a single statement of the form cout << '*'; (this causes the asterisks to print side by side). [Hint: The last two patterns require that each line begin with an ap- propriate number of blanks. Extra credit: Combine your code from the four separate problems into a single program that prints all four patterns side by side by making clever use of nested for loops.]
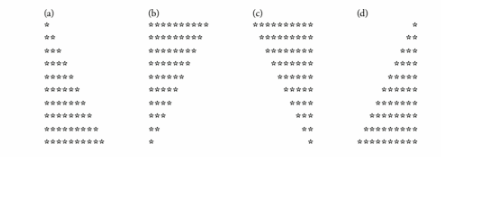
What will be an ideal response?
Click SmartArt in the Illustrations group of the ________ tab to select from the SmartArt categories
A) HOME B) DESIGN C) PAGE LAYOUT D) INSERT
? A _____ shows how data acts through an information system but does not show program logic or processing steps.
A. ?data flow diagram B. ?data tree diagram C. ?data model diagram D. ?data structure diagram