What are the two questions that a threat analysis should address?
What will be an ideal response?
Who might want to abuse this system? and Why would they want to do so? (That is, What will they do with the system that they should not?)
You might also like to view...
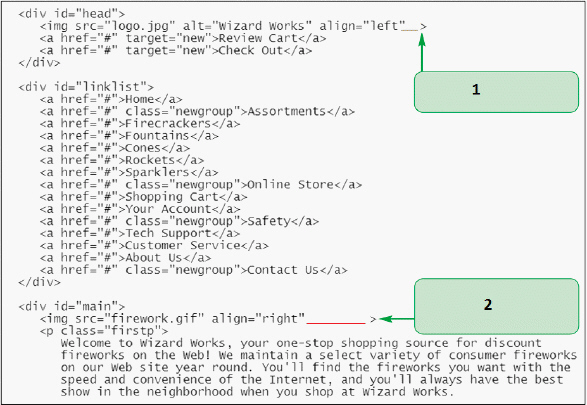 In the figure above, what do you need to add to fix the tag pointed at by item 1 under the strict DTD?
In the figure above, what do you need to add to fix the tag pointed at by item 1 under the strict DTD?
A. @ B. / C. -- D. !
Which of the following views is NOT available for mailing labels?
A) Report B) Print Preview C) Layout D) PivotTable
A typical Group Footer section will include which type of data?
A. a count or subtotal for records in that group B. the date and time the report was generated C. the report page number D. detail fields for all records included in the group
In an optical disc, the absence of light is read as binary digit 1.
Answer the following statement true (T) or false (F)