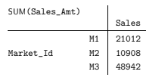
Compute the result table.
What will be an ideal response?
Computer Science & Information Technology
You might also like to view...
The _______ property of an event stores a reference to the control that triggered the event.
a) Target b) Source c) SourceControl d) EventTarget
Computer Science & Information Technology
Located to the left of the formula bar, the ________ displays the active cell reference
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Bill and John are overloaded. They have to install more than 50 access points. Joni hears their frustration and offers to help. This is an example of ____
A) Tag teaming B) Consolidation C) Teamwork D) Outsourcing
Computer Science & Information Technology
What encryption algorithm can be used for both encryption and digital signing, uses a one-way function, and is still widely used in e-commerce?
A. ECC B. RSA C. DES D. AES
Computer Science & Information Technology