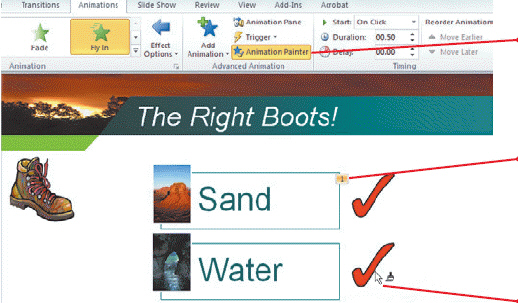
 The Animation Painter in the accompanying figure works just like the Format Painter in its transfer of text and graphic formatting to text and graphics.
The Animation Painter in the accompanying figure works just like the Format Painter in its transfer of text and graphic formatting to text and graphics.
Answer the following statement true (T) or false (F)
True
You might also like to view...
What is the value of x after the following statements?
int x; x = 15/4; a. 15 b. 3 c. 4 d. 3.75
Answer the following statements true (T) or false (F)
1. Asymmetric encryption utilizes only a public key for encryption and decryption. 2. Asymmetric encryption can be used for confidentiality but not for authentication. 3. Asymmetric encryption transforms plaintext into ciphertext. 4. Plaintext is transformed into ciphertext using two keys and a decryption algorithm. 5. A major advance in symmetric cryptography occurred with the development of the rotor encryption/decryption machine.
The ____ handles computer crimes that are categorized as felonies.
A. FBI B. U.S. Secret Service C. U.S. Treasury Department D. Securities and Exchange Commission
A class that implements an interface but does not declare all of the interface’s methods must be declared ________.
a. public. b. interface. c. abstract. d. final.