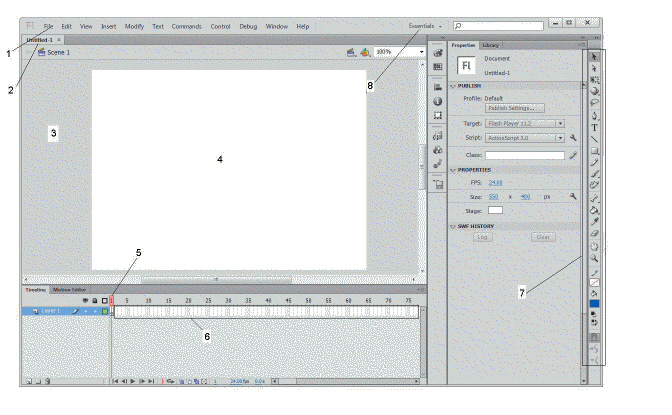
 The item marked ____ in the accompanying figure is the Tools panel.
The item marked ____ in the accompanying figure is the Tools panel.
A. 1
B. 5
C. 7
D. 8
Answer: C
You might also like to view...
When deleting a node from a binary search tree that has two children, the reason we can replace its element with the greatest value in its left subtree is because:
A. the value will become greater or equal to the values of its children B. the value will be greater than everything on its left, and since it was in the left subtree, it will be less than everything in the right subtree C. Both A and B D. Neither A nor B
Irrespective of the development strategy used, many organizations still rely on the IT group to provide guidance when it comes to selecting tools to support strategic planning activities.
Answer the following statement true (T) or false (F)
Identity thieves may target your ____.
A. Social Security number B. credit card and debit card numbers C. PINs and passwords D. all of the above
__________ are usually passive devices and can be deployed into existing networks with little or no disruption to normal network operations.
A. NIDPSs B. HIDPSs C. AppIDPSs D. SIDPSs