Your organization recently deployed a standard operating system image to all desktop systems and is now scanning the computers weekly against a security baseline. Which of the following cannot be learned by scanning against the baseline?
A. security settings that have been changed
B. user data that has been deleted
C. security policies that have been disabled
D. antimalware software that has been removed
B
Explanation: Because the data was not present in the image, then it cannot be detected as missing when the scan is run.
You might also like to view...
At a high level of abstraction, the BSIMM interpretation of governance is fundamentally different than SAMM's.
Answer the following statement true (T) or false (F)
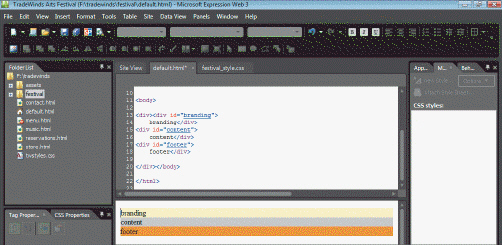 Referring to the figure above, the purpose of the div tag in this instance is to act as a container for ____.
Referring to the figure above, the purpose of the div tag in this instance is to act as a container for ____.
A. graphics B. images C. all other divs on the page D. All of the above.
An input device that increases the speed and accuracy of data entry and converts information into a digital format that can be saved, copied, and manipulated.
What will be an ideal response?
The most common type of Internet search is the ____.
A. keyword search B. character search C. directory search D. distributed search