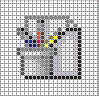
 In the associated figure, each colored dot is called a(n) ____.
In the associated figure, each colored dot is called a(n) ____.
A. pixel
B. bit
C. byte
D. analog
Answer: A
You might also like to view...
Which statement below is false?
a. Each JPopupMenu should be associated with its own component. b. Local variables must be declared static to be used in an anonymous inner class declaration. c. The JPopupMenu show method specifies the origin component, and the coordinates at which the JPopupMenu should display on the component. d. None of the above.
Match each item with a statement below.
A. software installed on a computer that produces pop-up ads using your browser B. a code used to identify and authenticate a person or organization sending data over a network C. A program that is potentially harmful or potentially unwanted D. type of spyware that tracks your keystrokes, including passwords E. an attack that can be used to crack a long password by trying words and word combinations F. the practice of tricking people into giving out private information or allowing unsafe programs into the network or computer G. when someone who is unauthorized follows the employee through a secured entrance to a room or building H. A type of malware that tricks you into opening it by substituting itself for a legitimate program I. a computer that has been hacked, and the hacker is using the computer to run repetitive software in the background without the user's knowledge J. an infestation designed to copy itself repeatedly to memory, on drive space, or on a network
Match the following terms to their meanings:
I. Some individuals will use this network to take A. VPN control of your computer II. A wireless network that does not require you to B. rogue network enter a passphrase III. Requires you to enter both the network name C. hidden network (or SSID) and passphrase IV. Requires you to enter a passphrase to access D. security-enabled network the network V. Organization's network within a network that E. unsecured network encrypts network traffic
?When comparing search engines, it is important to know the company's policy toward allowing commercial sites to boost their ranking in a _____ arrangement.
A. ?fee for service B. ?pay for none C. ?free for all D. ?pay for performance