Harassment others via the Internet, such as through email, text messaging, a social networking site, or other online communications method, is referred to as _________.
A. cyberbullying
B. cybersquatting
C. net spoofing
D. larceny spoofing
Fill in the blank(s) with the appropriate word(s).
cyberbullying
Rationale: Bullying others via the Internet, such as through email, text messaging, a social networking site, or other online communications method, is referred to as cyberbullying. Cyberbullying can take place openly, but often it occurs anonymously, such as a bully sending messages via a hacked social media or email account, or a bully hacking a victim's social media account and changing the content. See 6-5: Cyberstalking and Other Personal Safety Concerns
You might also like to view...
Answer the following statements true (T) or false (F)
1. One reason for using functions is to break programs into a set of manageable units, or modules. 2. If a function has no return statement, the flow of control moves to the next function in the file when the closing brace of the function body is reached. 3. When you make a function call, the order of the arguments you send does not matter as long as the number of arguments matches the number of parameters the function has. 4. Although global variables can be useful, it is considered good programming practice to restrict your use of them. 5. Both function headers and function calls must list the data types of all data being passed to the function.
With JPA, as part of a persistence unit, the IDE also creates a ________ package in the Source Packages folder.
a. META-DATA b. PERSISTENCE-INF c. PU d. META-INF
Fields can easily be renamed and their data types changed. By default, the ID field automatically created is assigned the __________data type.
A. Number B. Auto Number C. Text D. Short Text
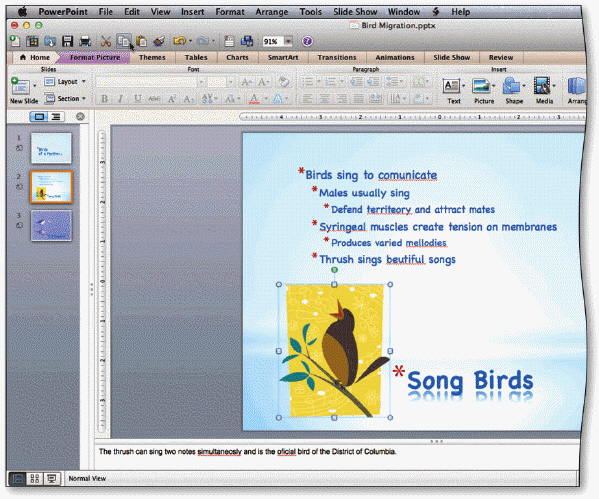 In the accompanying figure, words underlined with a red wavy line are possibly ____.
In the accompanying figure, words underlined with a red wavy line are possibly ____.
A. antonyms B. emphasized C. misspelled D. synonyms