People who are in your ________ network can share files that you have stored in your online Public folder
A) Hotmail B) Live Preview C) My Documents D) Windows Live
D
Computer Science & Information Technology
You might also like to view...
The term ____ refers to the fact that the programmer reviews the algorithm while seated at his or her desk rather than in front of the computer.
A. desk-checking B. program-checking C. desk-tracing D. hand-checking
Computer Science & Information Technology
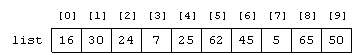 On average in a sequential search, how many comparisons would have to be made to find an element in the list in the accompanying figure?
On average in a sequential search, how many comparisons would have to be made to find an element in the list in the accompanying figure?
A. 2 B. 5 C. 6 D. 8
Computer Science & Information Technology
In order to provide support for the HTTPS protocol under LWP, we need the ____ Perl module.
A. LWP::UserAgent B. Crypt::HTTPS C. Crypt::SSLeay D. Crypt::SSLAgent
Computer Science & Information Technology
Give the coordinates and the quadrant or axis where point G is located. 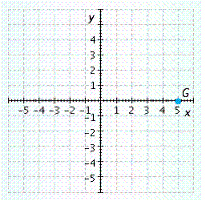
A. ![]() , x-axis
, x-axis
B. ![]() , y-axis
, y-axis
C. ![]() , x-axis
, x-axis
D. ![]() , x-axis
, x-axis
E. ![]() , y-axis
, y-axis
Computer Science & Information Technology