Assume double[][] x = new double[4][5], what are x.length and x[2].length?
a. 4 and 4
b. 4 and 5
c. 5 and 4
d. 5 and 5
b
You might also like to view...
Answer the following statements true (T) or false (F)
1. Kerberos provides a trusted third party authentication service that enables clients and servers to establish authenticated communication. 2. Examples of dynamic biometrics include recognition by fingerprint, retina, and face. 3. User authentication is the means by which a user provides a claimed identity to the system. 4. Identity federation is in essence an extension of identity management to multiple security domains. 5. User authentication is the basis for most types of access control and for user accountability.
A communications ____ is used for transporting data over a network.
A. gateway B. signal C. network hub D. channel
In the accompanying image of a Microsoft Word 2016 document, Box A points to the _____.?
?
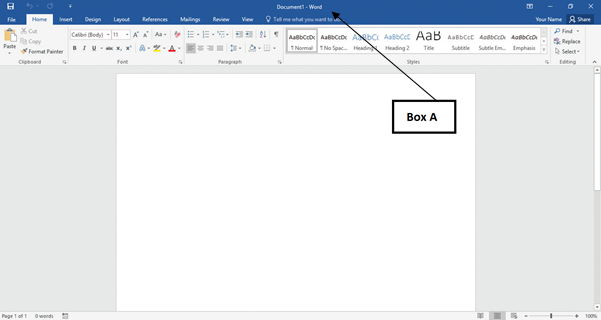
A. ?title bar B. ?status bar C. ?taskbar D. ?scroll bar
The ____________________ is the name of the court that has authority to rule with reference to specific persons or subject matter.
Fill in the blank(s) with the appropriate word(s).