The __________ determines what access should be granted.
A. authentication server
B. policy server
C. supplicant
D. access requestor
B. policy server
You might also like to view...
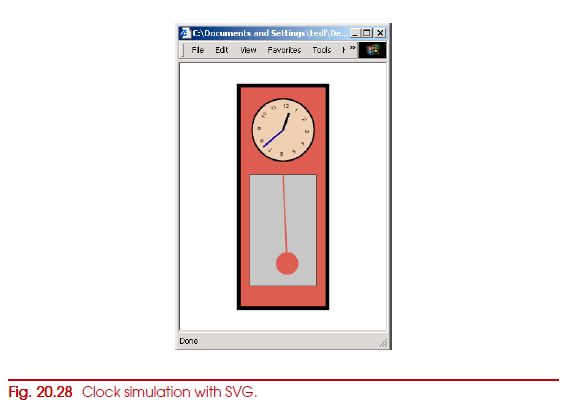
Create an SVG document that simulates a clock with a pendulum (i.e., hour hand, minute hand, pendulum). An example image is shown in Fig. 20.28.
Suppose that you have the declaration:int num = 94;double x = 73.92;String str = "Programming";What is the output of the following statements?System.out.println("123456789012345678901234567890");System.out.printf("%5d%6.2f %15s%n", num, x, str);
A. 123456789012345678901234567890 94 73.92 Programming B. 123456789012345678901234567890 94 73.92 Programming C. 123456789012345678901234567890 94 73.92 Programming D. 123456789012345678901234567890 94 73.92 Programming
In terms of copyright, Fair Use is determined to be
a. The use of a copyrighted work for purposes such as criticism, reporting, teaching, scholarship, or research. b. The use of anything you find on the Web c. Copying other's music and fairly distributing it to your friends d. None of the above
What type of design does the following activities belong to; UML, Wireframes, and prototypes?
A. Object Oriented B. Static C. Dynamic D. Secure